Go to Active Directory Users and Computers and create Security group. Open the properties of the newly security group, open the Members tab and add domain users which you want to assign VPN access to. This is all you need to configure on the server side. ASA configuration for LDAP authentication. Let’s move on to ASA configuration part. When using a Cisco ASA with the AnyConnect VPN Client software in some instances it is useful to assign the same static IP address to a client whenever they connect to the VPN. Within Active Directory you can configure per user a static IP address and use this IP address whenever the user connects to the VPN. The RADIUS Server (in this instance Cisco ISE 2.0) can be configured to query the attribute in AD which is the” msRADIUSFramedIPAddress” value and assign to the client whenever they.
Steps to restrict Cisco AnyConnect VPN login based on AD Group
Refer to Cisco AnyConnect VPN with CLI prior continue the lab below
AAA Group for LDAP Authentication
Create an AD GRoup named VPN and assign UAT1 as member of VPN Group
Create a Server Group (AD) for LDAP Authentication with Domain Controller (10.10.10.230)
Verify LDAP Authentication is working fine
Anyconnect Active Directory Authentication Failed
LDAP Attribute Maps
In order to use LDAP to assign a group policy to a user, you need to configure a map that maps an LDAP attribute, such as the Active Directory (AD) attribute memberOf, to the IETF-Radius-Class attribute that is understood by the VPN headend
Refer to Cisco Documentation – ASA Use of LDAP Attribute Maps Configuration Example for more detail information
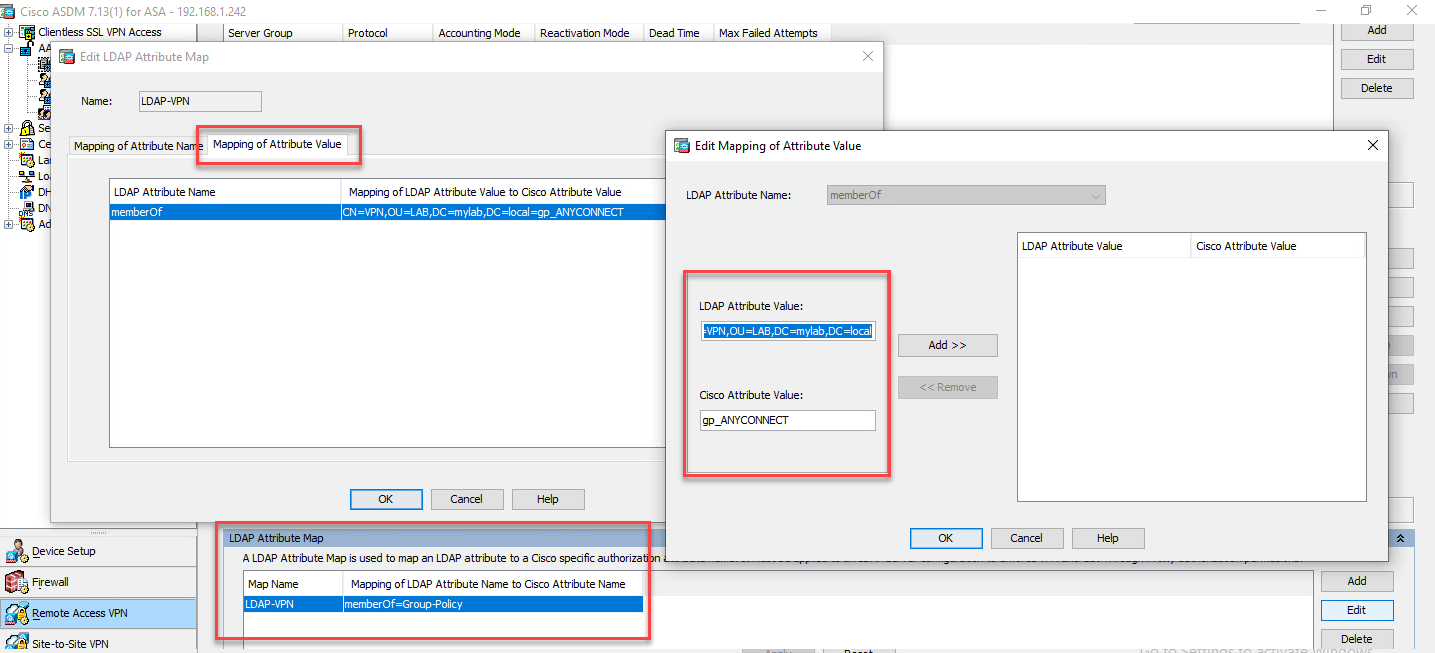
Create a LDAP Attribute Map (LDAP-VPN) to map AD Group (VPN) to gp_ANYCONNECT Group Policy (gp_ANYCONNECT)
AD Attribute is CASE SENSITVE in LDAP Attribute Map
New Group Policy – gp_NO-ACCESS
Create a New Group Policy (gp_NO-ACCESS) to DENY Users who are NOT member of VPN Group to login with vpn-simultaneous-logins 0
Update the existing Group Policy (gp_ANYCONNECT) with vpn-simultaneous-logins 500 (the number of allowed VPN Session)
Change the Default Group Policy to Tunnel Group
Modify the Tunnel-Group (prof_ANYCONNECT)
- To use AAA Group (AD) to authenticate AnyClient Client
- Change the Default Group Policy to gp_NO-ACCESS to DENY users who are not member of VPN Group to login
Assign ldap-attribute-map to AAA Group
Cisco Anyconnect Vpn Client Download
Assign ldap-attribute-map (LDAP-VPN) to AAA Group (AD)
Cisco AnyConnect VPN login based on AD Group – Member of VPN Group
Group Policy (gp_ANYCONNECT) is assigned to UAT1 who is member of VPN Group, and UAT1 is login successfully.
Cisco AnyConnect VPN login based on AD Group – Non-Member of VPN Group
Group Policy (gp_NO-ACCESS) is assigned to UAT2 who is NOT member of VPN Group, and UAT2 failed to connect with AnyConnect VPN Client
